What Is Financial Audit Readiness? Meaning, Benefits, and Checklist

Joseph Jacob
September 19, 2025 11 Min Read

See Savant AI Agents turn unstructured data into usable insights — live.
Register
AI and Automation Are Reshaping Finance, Tax, and Accounting — See How.
Download Now
Unstructured data slows finance and analytics. Watch the fix in our Fall Release webinar.
Save Your Spot

Every March, finance teams rebuild pivot tables, chase stray approvals, and hope the “provided-by-client” (PBC) list doesn’t grow overnight. That ritual made sense when audits were once-a-year snapshots. Today, regulators, customers, and investors expect near-real-time assurance, and the cost of falling short keeps rising. In 2025, the smarter move is to stay audit-ready year-round: build systems, documentation, and AI-powered safeguards so an auditor’s surprise visit feels like just another Tuesday.
Audit readiness is a continuous state: books are accurate, controls are documented, and current evidence is available for an external auditor at any time with minimal remediation. In practice, it means you can produce support, show who approved what and when, and demonstrate that controls operate as designed, all without a scramble.
Audit readiness is the ongoing work — the processes, policies, tooling, and assessments that keep you prepared.
Audit-ready is the outcome — evidence locked, controls proven, and stakeholders aligned. Think marathon training (readiness) versus race-day fitness (audit-ready).
Even well-run finance orgs feel the crunch once evidence requests start flying; here’s where the stress really comes from:
Audit readiness pays off operationally and strategically. On the cost side, standardized evidence and workflows in one system cut rework, reduce auditor follow-ups, and limit change orders, so fees and overtime come down. In fact, one Workiva customer reported about $300,000 in annual savings.
Close cycles become more predictable because support is captured as work happens. Access reviews are logged, journal entries carry their approvals and attachments, reconciliations include timestamps and preparer/approver trails, and exceptions route to owners with due dates. That discipline shrinks late adjustments, trims weekend sprints, and gives controllers clean variance narratives instead of detective work.
Readiness also accelerates outcomes that matter to leadership. Fundraising, M&A, lender renewals, and large-customer diligence move faster when you can grant data-room access to current policies and system logs that prove changes and approvals. Externally, auditors spend less time chasing artifacts and more time testing, which keeps engagements on budget; internally, finance, IT, and security work from a shared source of truth rather than spreadsheets and email threads.
Audit-readiness is also a form of future-proofing; as firms shift toward continuous, data-first audits, environments with automated evidence, clear lineage, and consistent monitoring adapt with far less disruption.
To make readiness repeatable, anchor your program to a few core elements; if one is weak, the whole structure wobbles.
Document policies, narratives, swimlanes, and data flows, then tag each artifact to the relevant COSO component (Control Environment, Risk Assessment, Control Activities, Information and Communication, Monitoring). Maintain a cross-reference matrix so every control and procedure traces to a COSO principle and to the evidence that proves it. Version documents, capture approver and effective dates, and store them in a system where auditors can see history without emailing for PDFs.
Define each control with a clear objective, frequency, owner, and the data used to perform it. Include walkthroughs, samples, and step-by-step procedures so that the control can be executed the same way regardless of who is on shift. For SOX 404, separate design and operating effectiveness testing; keep evidence packs with populations, selections, and results to show the control works as designed.
Treat system logs, reconciliations, and version history as part of the control framework. Show how a journal line or report figure ties back to source data with unbroken lineage across ETL jobs, transformations, and postings. Use immutable logs or append-only storage for change records, capture checksums where possible, and attach source evidence to entries so a reviewer can click from number to document in one path.
Keep a current risk register with IDs, descriptions, likelihood/impact scoring, control mappings, and owners. For every open gap, record the remediation plan, target date, and interim compensating controls; when closed, attach before/after evidence and note who validated the fix. Review the register on a monthly or quarterly cadence and re-score risks after major system or process changes.
Put finance, IT, security, and audit on a single source of truth for controls, evidence, and requests. Standardize intake (tickets or forms), define SLAs for evidence pulls, and publish the close calendar with dependencies so teams see what’s due and when. Hold short readiness checkpoints to clear blockers, and track a few simple KPIs like on-time evidence rate, exception aging, and rework, so leadership can see progress without sifting through spreadsheets.
These frameworks serve different purposes, and they stack. Understanding the distinctions between them keeps scope, testing, and evidence under control.
Many teams run both at once. The practical move is to “stack” them. Define the SOC 2 system boundary and SOX in-scope processes, map a common control library to COSO and the Trust Services Criteria, and keep evidence in one place so the same access reviews, change records, and logs satisfy both. Managing both frameworks multiplies evidence requests, control testing, and board scrutiny.
If the patterns below look familiar, your environment will struggle under audit pressure and external timelines.
Use this checklist (summarized in a table below) to move from ad-hoc scrambling to an always-on audit posture. It outlines a practical six-month run that clarifies who does what, what to produce, and what to automate. The aim is simple: Reach year-end with version-locked documentation, traceable support, and a live readiness dashboard so that fieldwork feels routine instead of disruptive.
Kick off with a working session. Confirm which frameworks apply (SOX 404(b), SOC 2, and any ESG requirements), and agree on in-scope processes. Loop in the external auditor early for scoping so nothing surprises you later. Run an initial gap scan to flag missing policies, stale access reviews, and unclear ownership.
Have process owners narrate workflows while an analyst records screens and compiles a knowledge base. Centralize policies, flowcharts, narratives, and control matrices in a version-controlled repository. Stage early evidence — bank reconciliations, journal approvals — into folders named to match the auditor’s PBC codes to avoid the spreadsheet maze later.
Convert risk findings into tickets with a clear “definition of done.” Typical fixes: close orphaned admin accounts, enable three-way match in AP, add security/privacy language to onboarding. Start automation pilots.
Have internal audit role-play the external team. Issue a sample PBC list, time responses, and grade clarity. Address gaps quickly (e.g., a subsidiary storing contracts on a local drive).
With core fixes shipped, turn on continuous analytics. Track simple KPIs: on-time evidence rate, exception aging, and control execution coverage.
Thirty days before year-end, freeze evidence folders and version-lock documents. Any late adjustments trigger an automated re-export with updated support. A readiness dashboard shows control execution and overdue approvals. When the external team arrives, grant self-serve portal access instead of stitching PDFs at midnight. The result: Fieldwork wraps sooner, overtime drops, and leadership spends the week on planning, not firefighting.
| PHASE | KEY ACTIONS | TYPICAL TIMELINE |
| 1. Scope the mission | Confirm frameworks (SOX 404(b), SOC 2, ESG), agree in-scope processes (order-to-cash, procure-to-pay, payroll, close), invite auditors to early scoping, run an initial gap scan (policies, access reviews, ownership). | Month 0–1 |
| 2. Document and diagnose | Record workflows, centralize policies/flowcharts/control matrix in version control, stage early evidence (bank recs, JE approvals) into PBC-coded folders. | Month 1–2 |
| 3. Gap remediation sprint | Convert findings to tickets with “definition of done,” close orphaned admins, enable three-way match, update onboarding language; start automation pilots. | Month 2–3 |
| 4. Mock walkthroughs | Internal audit runs a sample PBC (~40 items), times responses, fixes gaps (e.g., local-drive contracts). | Month 3–4 |
| 5. Continuous control testing | Turn on continuous analytics; track KPIs (on-time evidence, exception aging, control coverage). | Month 4-5 |
| 6. Lock, load, and breathe | Freeze evidence folders, version-lock docs, auto re-export on late adjustments, publish readiness dashboard, grant portal access, lock the fieldwork schedule. | Month 5–6 |
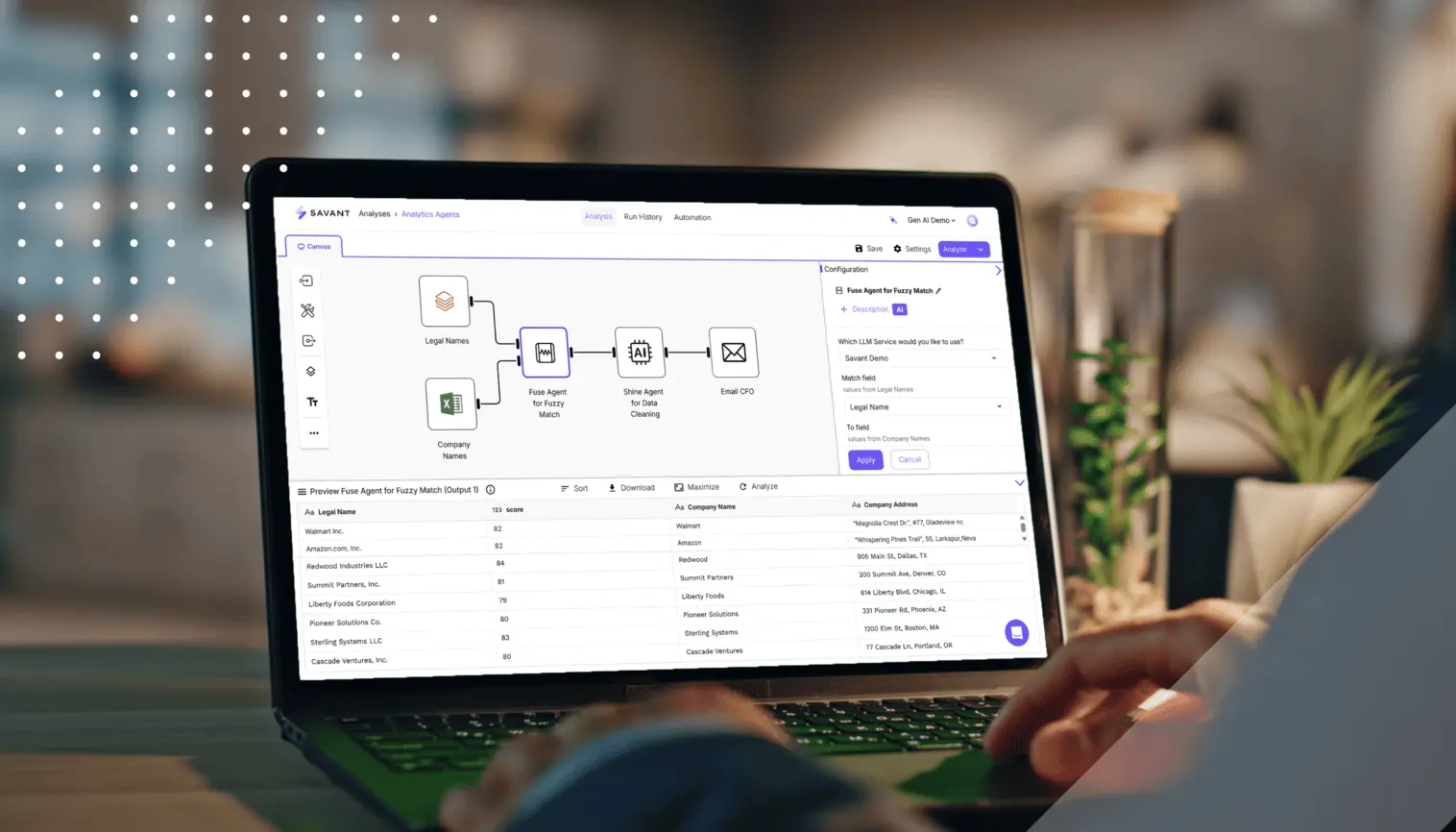
Savant ships with its Agentic Analytics SuiteTM — a suite of coordinated, specialized, purpose-built agents that plug into your finance stack. Each agent focuses on a narrow job — ingesting and classifying evidence, resolving entities, packaging audit support, etc. — and they share a common metadata layer so that context travels with the work. These agents run inside Savant’s no-code environment and learn your preferences via Savant’s industry-first Intelligence Graph™, so outputs stay aligned to your business context.
The result is a review-first flow: evidence is captured as activity happens, exceptions are routed with reasons, and auditors can self-serve from a traceable, versioned archive.
| SAVANT AGENT | WHAT IT DOES | AUDIT PAYOFF |
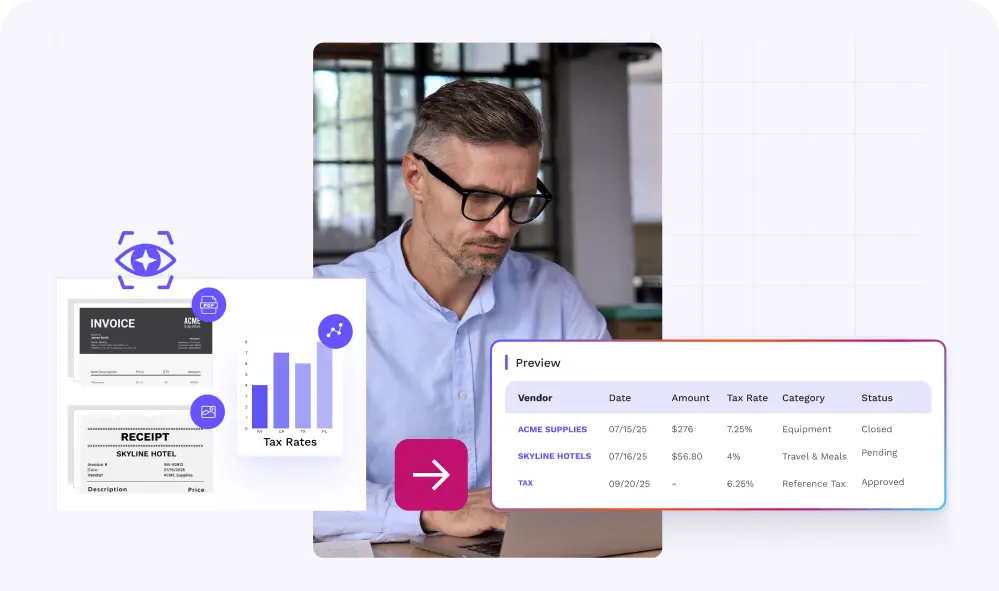
| Vision | Performs OCR/extraction from PDFs, images, and multi-page documents. Auto-extract data from GL recs, invoices, and more. | Makes it easier to attach source support (contracts, invoices, minutes) to controls and samples with the fields auditors ask for readily available. |
| Fuse | Intelligently fuzzy-matches records across systems; understands acronyms and variations; scores similarity, improving as it learns your patterns. | Creates clean, deduplicated populations (e.g., vendor master, counterparties), reducing false duplicates and name variants before sampling or JE testing. |
| Glean | Identifies trends and anomalies, compares metrics across periods, and surfaces significant changes; can generate plain-language summaries. | Supports a full-population monitoring mindset — daily anomaly surfacing with reasons/context helps teams remediate issues before fieldwork. |
| Stylus | Auto-documents workflows/analyses, makes artifacts searchable/discoverable, and tracks lineage/dependencies for reuse. | Centralizes process/evidence documentation so auditors self-serve current narratives, lineage, and references. |
| Infer | Enriches/completes incomplete records using business logic and context; applies rules consistently and flags uncertainties for human review. | Produces complete, standardized datasets (IDs, dimensions, categories) so populations used for testing are accurate. |
| Shine | Cleans and standardizes data (e.g., names, addresses, contact details) at scale while applying your formatting rules and handling edge cases. | Improves data quality and consistency in evidence sets (invoices, vendor files, reconciliations), cutting manual fixes during PBC pulls and walkthroughs. |
Audit readiness is not a once-a-year scramble, but an always-on posture that slashes costs, protects reputation, and frees talent for strategic work. Audit week shouldn’t hijack the quarter. Treat readiness as a daily habit: capture evidence where work happens, run controls on schedule, and keep a clear trail from number to source. When that rhythm is in place, fieldwork feels like a status check, not a crisis.
Savant’s agents handle the high-volume work of ingestion, reconciliation, and evidence packaging in the background. Combine disciplined processes with Savant’s ability to extract, reconcile, and document evidence, and finance leaders can greet auditors any day of the year with clean books, rock-solid controls, and confidence.